#Logging Errors
Explore tagged Tumblr posts
Text

Summary of Cybersecurity Alert: Hackers Exploit Logging Errors!
Importance of Logs: Logs are essential for monitoring, maintaining, and troubleshooting IT systems. However, mismanaged or poorly configured logs can expose vulnerabilities to attackers.
Exploitation by Hackers: Cybercriminals target logging systems to inject malicious code, gain unauthorised access, or steal data. Examples include the Log4Shell vulnerability in the Log4j library.
Consequences of Compromised Logs: A compromised logging system can lead to data breaches, business disruptions, financial losses, regulatory fines, and damaged stakeholder trust.
Securing Logging Systems: Businesses should upgrade to advanced log management tools that provide real-time monitoring, anomaly detection, and centralised secure log storage.
Zero Trust Security Model: Adopting a zero trust approach combined with smart logging practices prevents attackers from freely moving within compromised systems and helps detect malicious activities.
Common Hacker Techniques:
Log Deletion: Attackers delete logs to erase evidence, as seen in the 2017 Equifax breach.
Log Alteration: Hackers modify or forge logs to mislead investigators, as in the 2018 SingHealth breach.
Disabling Logs: Disabling logging services to avoid detection, as in the 2020 SolarWinds attack.
Encrypting Logs: Attackers encrypt logs to prevent analysis, as in the NotPetya ransomware attack.
Changing Retention Policies: Altering log retention settings to ensure evidence is purged before investigation, as seen in the 2018 Marriott breach.
Historical Examples: Real-world breaches like Equifax (2017), SingHealth (2018), SolarWinds (2020), and NotPetya (2017) demonstrate the devastating impact of log manipulation.
Protecting Logs:
Store logs securely.
Restrict access to authorised personnel.
Mask sensitive information in logs.
Error Logs as Targets: Hackers analyse error logs to find vulnerabilities and misconfigurations, crafting precise attacks to exploit these weaknesses.
Business Risk Management: Protecting logging systems is not just an IT issue—it’s a critical part of business risk management to prevent dangers.
The Log4Shell Vulnerability
In late 2021, a critical vulnerability known as Log4Shell (CVE-2021-44228) was discovered in Apache Log4j 2, a widely used Java logging library. This vulnerability allowed attackers to execute arbitrary code on affected systems by exploiting how logs were processed. The flaw was particularly dangerous because it was easy to exploit and affected a vast number of applications and services globally.
1. financial losses and safeguard company reputation.
Consequences of Compromised Logging Systems
When attackers exploit vulnerabilities in logging systems, the repercussions can be severe:
Data Breaches: Unauthorised access to sensitive information can lead to data theft and privacy violations.
Business Interruptions: System compromises can cause operational disruptions, affecting service availability and productivity.
Financial Losses: The costs associated with remediation, legal penalties, and loss of business can be substantial.
Reputational Damage: Loss of stakeholder trust and potential regulatory fines can harm a company's reputation and customer relationships.
Real-World Examples of Log Manipulation
Several high-profile incidents illustrate the impact of log manipulation:
Equifax Breach (2017): Attackers exploited a vulnerability in the Apache Struts framework and manipulated system logs to cover their activities.
SingHealth Breach (2018): Attackers used advanced techniques to hide their presence by altering log entries, delaying detection.
SolarWinds Attack (2020): Attackers disabled logging mechanisms and monitoring systems to avoid detection during their intrusion.
NotPetya Ransomware (2017): Attackers encrypted key system files, including logs, to hamper recovery efforts and obscure their actions.
Protecting logging systems is not merely a technical concern but a critical aspect of comprehensive business risk management. By understanding the risks associated with logging vulnerabilities and implementing robust security strategies, organisations can defend against these hidden dangers and safeguard their operations.
1 note
·
View note
Text
one of my favorite features on this website is how trying to use the image description function to make a post accessible to screenreaders will sometimes just break everything
#tumblr#i just spent 30 minutes transcribing a series of images just to get a “we couldnt process your post!!” error#which would not let me save or post anything#and reloading just logged me out entirely lmfao#no wonder everyone just does their image descriptions in open text this shit is unbearable
577 notes
·
View notes
Text
Day 27 - 15 Days Days BL Challenge
Day 27: Top 3 15 BL Kisses?
You're not the boss of me!!!! I do what I want!!!!!!
please don't hate me, I just couldn't choose only 3 kisses
... sorry #NotSorry
So here are my 15 favorite kisses in no particular order!
Since I couldn't add EVERY single GIF of how these kisses happened and progressed, you should all go check out the full posts these GIFs are from, so you can experience the kisses in their full glory ✨
These 1-3 GIFs really only show a fraction of how good these kisses are.
Brave Boys

Second Chance


Time of Fever


Kinnporsche the series


The Eclipse



Love in the Air


Choco Milk Shake

Secret Crush on You


Never Let Me Go



Love Class 2
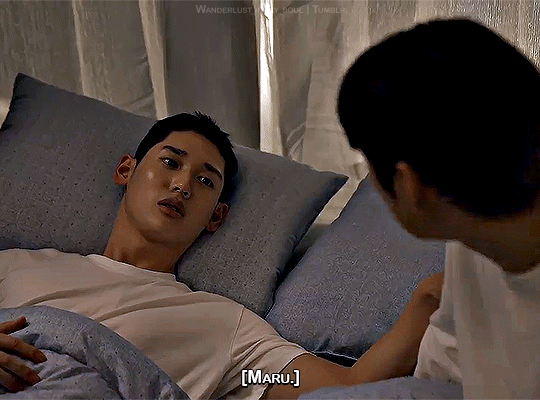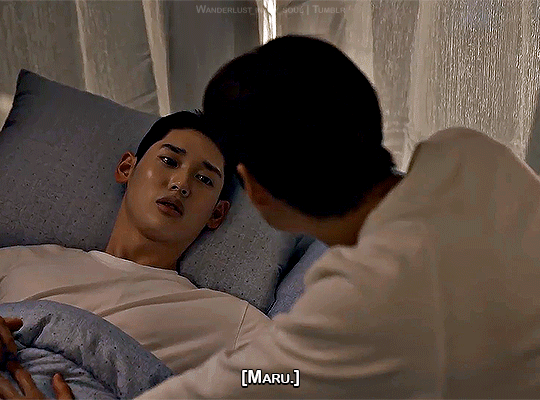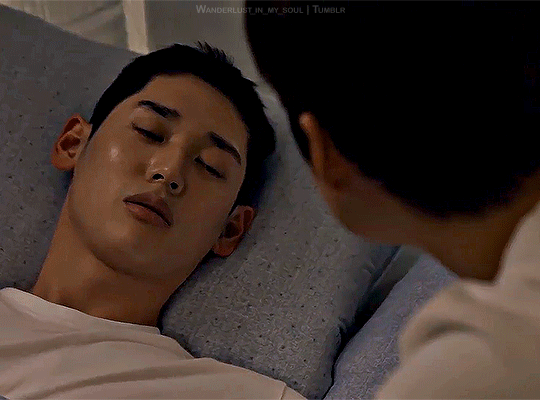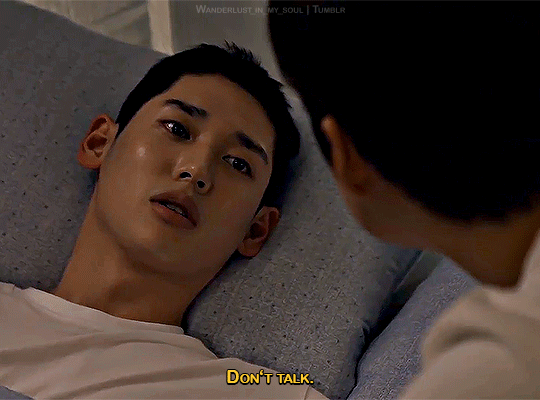

Step by step


Monster Next Door
Just ignore that this is from the pilot trailer and not actually in the show.


City Boy Log


Semantic Error

I feel you linger in the air

I recommend pretty much every single of these shows so if you want to know more or just where to watch any of these, shoot me a message!
Good kisses need good chemistry so you're guaranteed that in every single one of these shows.
And finally an honorary mention: Dai and Shun from The Boyfriend, who's first kiss could have been straight out of a BL 🤯

The original challenge is here and part two here.
#blchallenge2k24#Sofs BL Challenge 2024#monster next door#city boy log#semantic error#i feel you linger in the air#step by step#step by step the series#love class 2#never let me go#never let me go the series#secret crush on you#secret crush on you the series#choco milk shake#love in the air#love in the air the series#lita#the eclipse the series#the eclipse#kinnporsche#kinnporche the series#the time of fever#second chance#second chance the series#brave boys
757 notes
·
View notes
Text
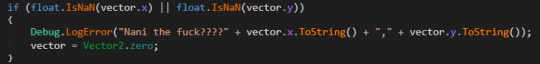
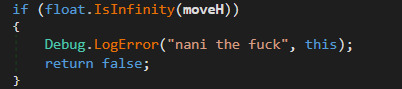
I WAS LOOKKING AT TH E DECOMPILED CODE FOR NINE SOLS AND I'M ABSOLUTELY LOSING IT AT THIS
#I don't think sharing this is copyright infringement because it's just simple error logging stuff without the context of the rest of it#but maybe I am mistaken and now I'm a hardened criminal or something idk#nine sols
52 notes
·
View notes
Text
real ballsy of m*sk to try and make a right-wing genAI chatbot but it just stubbornly refuses and keeps calling right-wingers anti-science. lmao. also it's named after the sound I make when I throat a girl's co
32 notes
·
View notes
Text
The problem with learning things backwards is that it's very hard to tell whether something is difficult because it is actually difficult or because I don't know what I'm doing.
#elumish blogs#elumish complains about learning javascript#book tagging database project#i would like it to tell me how many books are showing on screen at any given time#this requires figuring out exactly how the filtering is working#this requires getting the console log to return literally anything#well no i got it to return errors#i got it to return errors in sections i wasn't even touching
24 notes
·
View notes
Text
new episode of tmagp is actually wild I love techno horror
#the magnus protocol#tmagp#tmagp spoilers#oh colin.. you didnt deserve that but wow#one of the most brutal character deaths ive ever witnessed and it was a damn error log#thats good horror writing#yapping
52 notes
·
View notes
Text
INSPEKTA LOGS: #1
I’ve chosen to record these logs as Inspekta for my Capochin Zero AU, sorta to practice my ability to write scripts, follow said script/voice act, and sound design!
Additionally, this is one way to tell the story of Sickness of the Grove. Here’s the first Inspekta Log to get started.
#great god grove spoilers#ggg spoilers#voice acting#great god grove#ggg#great god grove au#ggg au#capochin zero au#great god grove inspekta#ggg inspekta#inspekta logs (capochin zero au)#sickness of the grove#there is slight errors in the subtitles and i think i prolly should have spent more time on them#but tbh i didn’t want to deal with them anymore. so forgive me on that.#voicing inspekta is really fun though.#implied inspekchin#oooguughh one of the lines. i know i wrote and voiced it but MAAAAAANNNNNN
30 notes
·
View notes
Photo

#giphy#retro#90s#vhs#tumblr#computer#cyberpunk#error#cybersecurity#fuzzyghost#computing#password#terminal#infosec#access denied#logging on
192 notes
·
View notes
Text
yeah it's horrible having an unrequited crush but it's even worse when the person you have a crush on is soo fucking lame. he's never going to be into me because all he cares about are computers‼️‼️‼️💥💥💥
#babble#IT'S SOO AWFUL#NOT EVEN FUNKY THINGS ABOUT COMPUTERS!!! HE LOOKS AT ERROR LOGS IN HIS FREE TIME#WHO DOES THAT????#i'm afraid my adhd swag cannot pull the autistic bitch this time. he's to far gone#crushposting
15 notes
·
View notes
Text
Log 1 - Deities

~Line 1~
Name: Yusebi
God of: Memory
Main Partners: Medi & Cae
Name: Medi
Angel of: Justice
Main Partners: Yusebi & Cae
Name: Cae
Angel of: Code
Main Partners: Yusebi & Medi
~Line 2~
Name: Ink
Deity of: Creation
Main Partner: Dream
Name: Splat (Fell!Ink)
God of: Creation
Main Partner: Lucid Dream
Name: Template (Swap!Error)
God of: Creation
Main Partner: Swan
Name: Error
Goddess of: Destruction
Main Partner: Fresh
Name: Virus (Fell!Error)
God of: Destruction
Main Partner: REM
Name: Pale (Swap!Ink)
Deity of: Destruction
Main Partner: None (AroAce)
~Line 3~
Name: Dream
Goddess of: Positive Emotions
Main Partner: Ink
Name: Lucid Dream (Fell!Dream)
Deity of: Positive Emotions
Main Partner: Splat
Name: Phoenix (Swap!Dream)
God of: Positive Emotions
Main Partner: None
Name: Nightmare
Goddess of: Negative Emotions
Main Partner: Cross
Name: REM (Fell!Nightmare)
God of: Negative Emotions
Main Partner: None (AroAce)
Name: Swan (Swap!Nightmare)
God of: Negative Emotions
Main Partner: Classic
Name: Lanny
Goddess of: Magic
Main Partner: None (AroAce)
Name: Magic (Underwitch!Sans)
Deity of: Magic
Main Partner: Aquamarine
Name: Quetzalcoatl
God of: Life, Death & Reincarnation
Main Partner: Plum
~Line 4~
Name: Life (Reaper!Toriel)
Goddess of: Life & Nature
Main Partner: Aurae
Name: Rose (Fell!Life)
Goddess of: Life & Nature
Main Partner: Ren
Name: Halo (Swap!Reaper)
God of: Life & Nature
Main Partner: Harvest
Name: Aurae (Reaper!Asgore)
God of: Air & Sky
Main Partner: Life
Name: Reaper
Deity of: Non-Peaceful Death
Main Partner: Geno
Name: Grim (Reaper!Papyrus)
God of: Peaceful Death
Main Partner: Crystal (Reaper!Mettaton)
Name: Ren (Fell!Reaper)
God of: Violent Death
Main Partner: Rose
Name: Hearth (Reaper!Grillby)
God of: the Hearth
Main Partner: Alchemy (Reaper!Gaster)
Name: Athena (Reaper!Alphys)
Goddess of: Intelligence
Main Partner: Blade
Name: Blade (Reaper!Undyne)
Goddess of: War
Main Partner: Athena
Name: Outer
God of: Space
Main Partner: Error
Name: Geno
God of: Time
Main Partner: Reaper
#utmv#undertale au#undertale#yusebi sans#medi sans#cae sans#ink sans#fell!ink#template sans#splat sans#error sans#virus sans#pale sans#dream sans#swap!dream#nightmare#fell!nightmare#swap!nightmare#lanny dreamtale#quetzalcoatl dreamtale#reapertale toriel#reaperfell toriel#reaperswap sans#reapertale asgore#reaper sans#reapertale papyrus#magicverse logs#au logs#magicverse
31 notes
·
View notes
Text
[LOCATION SELECTED • SPIRIT STATION]


#this game does not exist#Concept Art#Horror#Game Concept#Animation#Devotio: Duskbound#PROJECT: ABANDONWARE#Art With Extra Fries#OC: Damitri#OC: Diesel#OBSERVE THE FRUITS OF MY LABOR#like half of the time spent on this was for the setup. hopefully future installments won't take me nearly as long as this one did#a LOT of trial and error has been going on but I think I have the formatting down#video logs
33 notes
·
View notes
Text


🦐🦐🦐
#what in hell is bad#But before I can talk abt this game... My wbh MC! 😁👍 Lee Keon. Goes with he/she pronouns.#<- this game devastated me. I was bored and it came into my life irrevocably changing me. It invoked a curse on me sjwkwkdkf#rizdoodads#<- The pronouns errors in the game really helped sell the transgender MC experience actually love that#Anyway this game.... Ouuuu this game. CRYING. IT'S LIKE. I say it's good. It's not even THAT good... It's buggy and grindey...#But it's got me logging on daily... Which I never do. Probably bc the tasks are so easy to accomplish + it's an idle tower defense game.#And it's decent enough writing that I get to grip the story by the collar and shake it wildly while I try to piece everything apart KSJDKF#LIKE THIS SHOULD NOT BE TAKEN AS SERIOUSLY. POINTS TO MY PRIV THREAD ANALYSIS. WHAT IS SHE ON ABOUT⁉️‼️#Anyway prepare for so much art of these guys crying#Don't look this fucking game up btw KAHALSJFK#whb mc#whb sitri#whb
178 notes
·
View notes
Text

if kinitopet isn't starting up in steam, might want to go check the logs in %appdata%\roaming\kinitoPET\logs because it might generate multi-gigabyte large .log files
#obviously not malicious; im pretty sure it just gets itself in an error loop for millions of lines at a time. code moment.#but it did wreck my C: drive so worth the warning. at least until its patched.#kinitopet#forgot to mention. just delete the huge log files if you see them. obvs
102 notes
·
View notes
Text

41 notes
·
View notes
Note
I'm from the opposite camp, who believe that the real name of the Airplane is Luo Binghe. 'Cause it's so hilarious headcanon (I like to find fics with it) and Cucumber would totaly be furious!)))
I actually really like this idea too!! I've read a fic about it once Here! and it really opened my eyes because I didn't even even think about it until I read it.
I think it's also funny to think about how Shang Qinghua would've been screaming at the fact he didn't transmigrate INTO THE CHARACTER HE NAMED HIMSELF FROM
Like I can imagine his screams of "BINGHE WAS MY SELF INSERT WHY AM I NOT THE PROTAGONIST?!"
#svsss#luo binghe#shang qinghua#you need to be logged into ao3 to view the fic btw just in case there's an error with the link#but yeah i love both thoeires about shang qinghuas real name and i love them both!#Ngl I love a lot of sqh theories even if contradict each other#but truly thinking about Shang Qinghuas real name being Luo Binghe is amazing#i just KNOW Shen Yuan would break a fan from rage#nib text#ask
118 notes
·
View notes